Security Management
When you generate an SSL Certificate that is required by HTTPS, you are creating a keystore file and a keystore password for use when the browser interface connects to the Master Server. For client applications to consume secured services hosted from a standalone Rice server, the implementer must generate a keystore in KSB. KSB security relies on the creation of a keystore using the JVM keytool.
You can choose whether to have a Certifying Authority sign the certificate or you can use a self-signed certificate. A certificate signed by a Certifying Authority is trusted by browsers, therefore the browser does not issue a warning when a user connects to the browser interface on the Master Server.
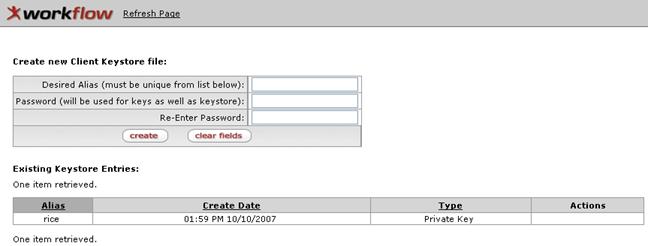
 To
create a new client keystore file:
To
create a new client keystore file:
• Type your Desired Alias (keystore name).
• Type your Password.
• Re-Enter Password.
• Click create.
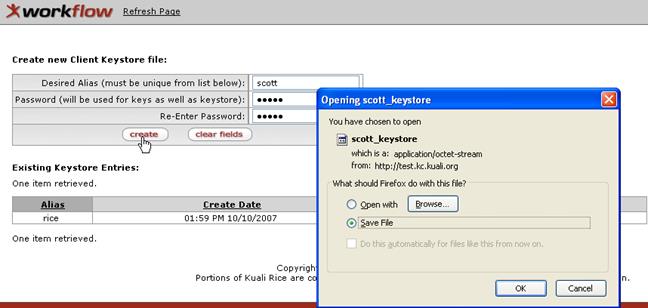
• Save the file locally as desired.
The keystore you created is displayed in the Existing Entry table:
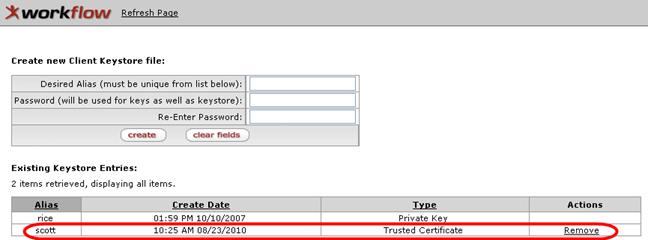
The Trusted Certificate you created is available for immediate use after being generated because it is not necessary to wait for a certifying authority to sign it.
|
|
The Desired Alias (name for the new keystore you are creating) must be unique among your keystores. KSB automatically displays a list of existing Keystore entries for your reference below the Create new Client Keystore file table. The data in this list can be sorted in ascending or descending order by clicking the column heading for any column except Actions. erts you to supplementary information that is useful to the completion of a task. |
 For more
information, see “Embedded Mode” on page
29 in Downloading, Installing, and Configuring.
For more
information, see “Embedded Mode” on page
29 in Downloading, Installing, and Configuring.
